Do you know myorbik .com?
Welcome to myorbik.com, your essential companion in finding and understanding vulnerabilities in embedded systems. This revolutionary application has been designed to provide a detailed and comprehensive view of the security of your systems, scanning and collecting various vulnerabilities with precision.
myorbik.com is officially online!
Boost your Business with myorbik.com
Automate Product Vulnerability Management
Our tool automates the process of managing product vulnerabilities, streamlining operations and enhancing efficiency.
Cost Reduction, compared to manual methods
Utilizing myorbik.com significantly reduces costs, making vulnerability management more affordable for businesses of all sizes.
Integration with Open Source Tools
myorbik.com seamlessly integrates with various open- source tools, automating tasks and enhancing overall functionality.
Cost Savings
Companies can experience up to a fivefold reduction in costs by utilizing myorbik.com, providing significant savings without compromising on quality or effectiveness.
Error Prevention and High-Fidelity Management
By automating tasks and eliminating human errors, myoribk.com ensures high-fidelity vulnerability management, enhancing accuracy and reliability.
Vulnerability monitoring
The website myorbik.com redefines IT security by taking a proactive approach through its advanced vulnerability monitoring. Instead of waiting for threats to manifest themselves, myorbik.com constantly scans the digital landscape, identifying and assessing potential points of vulnerability. The application performs regular, comprehensive scans of systems, networks and applications, using sophisticated algorithms to detect even the most subtle threats. Continuous monitoring ensures that new vulnerabilities are identified in real time, providing users with the ability to mitigate risks before they become significant threats.
Vulnerability management
The tool myorbik.com simplifies vulnerability management through automatic and scheduled scans. Establish regular intervals to assess and update the security of your systems, ensuring a constant and adaptive defense against emerging threats. We understand that not all vulnerabilities are equal in terms of risk. myorbik.com uses intelligent prioritization criteria to rank threats based on their severity and potential impact on your digital infrastructure. This allows you to focus on addressing critical vulnerabilities first.

Centralization of information
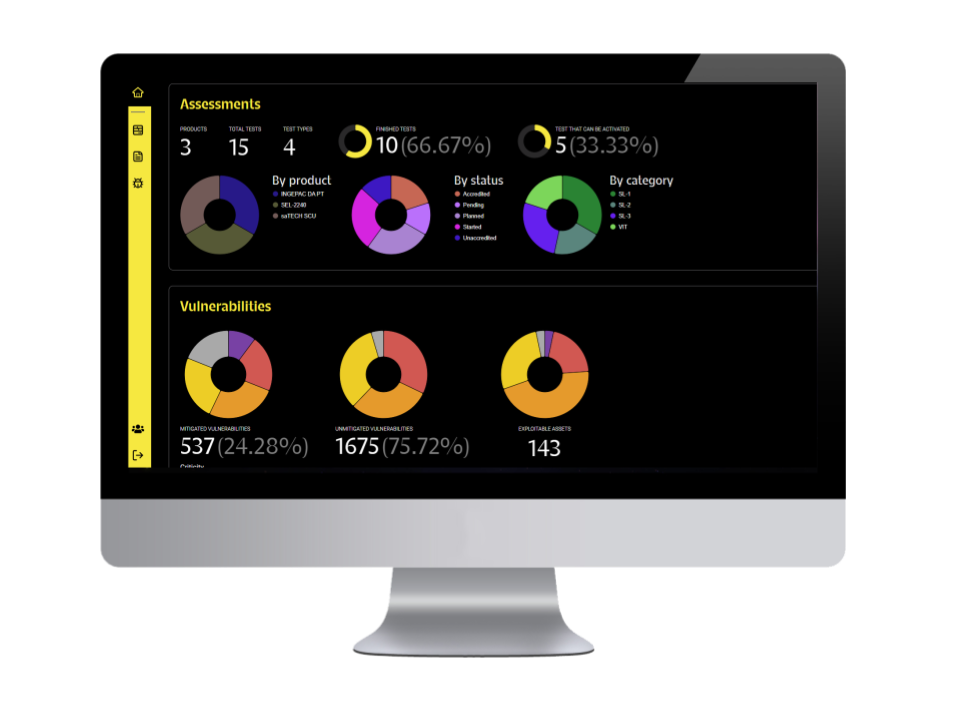
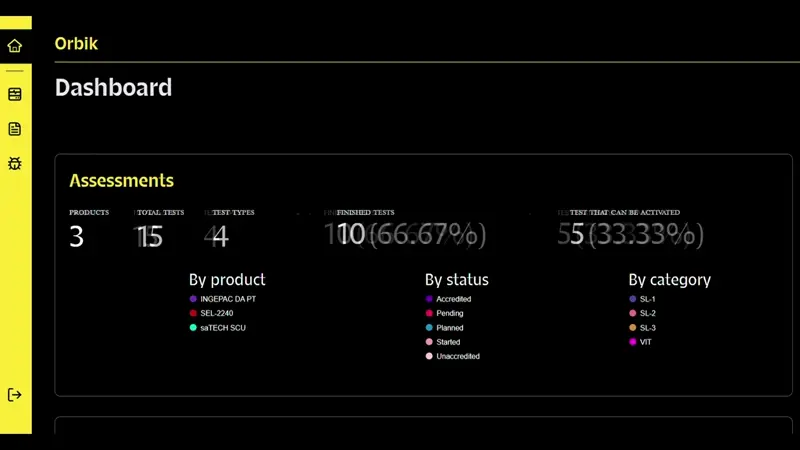
The application not only identifies vulnerabilities, but also centralizes information efficiently. myorbik.com organizes the findings in a clear and accessible way, providing users with a unified view of the security posture of their systems.
SBOM Quality Metrics
Software Bill of Materials (SBoM) quality metrics enhance vulnerability management tools by ensuring SBOM accuracy, completeness, timeliness, consistency, standard compliance, and risk prioritization.
These metrics provide precise, comprehensive, and current data on software components and vulnerabilities, aiding informed decision-making, efficient remediation, and improved cybersecurity by prioritizing actions based on severity and impact.


Benchmark
Comparing vulnerabilities between two products serves as a benchmark, enabling evaluation of their relative security. It informs decisions on adoption and highlights risks and security issue frequencies. Additionally, it motivates developers to enhance security measures based on unfavorable comparisons. 🚀
Set up Your Security Feed and Alerts with Emailed Reports
myorbik.com securely maintains current SBOMs of your products and continuously rescans and tracks vulnerabilities for all your product is released and in production.
- Stay on top of new vulnerabilities periodic rescans and reports.
- Keep your device secure in the field, for full product lifecycle.


Integration with scanning tools
Our platform now supports seamless integration with leading scanning tools including Nessus, Acunetix, BurpSuite, and Achilles. This feature enables users to effortlessly incorporate these powerful tools into their cybersecurity workflows, enhancing their ability to identify, assess, and mitigate vulnerabilities.
Cyber Resilience Act Self-Assessment Tool with Our Support
Our platform now features a comprehensive Cyber Resilience Act self-assessment tool, designed to help organizations evaluate their compliance with the latest cybersecurity regulations. This tool provides a structured framework for assessing your cyber resilience, identifying potential gaps, and implementing necessary improvements. With our dedicated support team available to guide you through the process, you can ensure that your organization meets the required standards and strengthens its overall security posture. This feature simplifies the path to compliance, offering expert advice and actionable insights every step of the way.

Outdated Component Analysis
Using components with known vulnerabilities in a supply chain poses significant risks to dependent projects. However, even components without known vulnerabilities, but which are not the latest release, present several risks. Many vulnerabilities that are discovered and fixed are never reported through official channels or are reported much later. Consequently, using components with unreported vulnerabilities still exposes projects to risk. Additionally, the likelihood of vulnerabilities being reported against a component is high.
Components may undergo minor or significant API changes between releases, making it crucial to keep them updated. Regularly updating components ensures that organizations benefit from performance, stability, bug fixes, new features, ongoing community support, and can quickly respond to security events when vulnerabilities are discovered. By maintaining up-to-date components, organizations are better prepared to address security threats with urgency and efficiency.

Other myorbik.com features

Incident Response
Vulnerability Prioritization
Proactively identify and prioritize vulnerabilities based on their potential impact to your organization. Receive targeted alerts when new threats emerge, enabling rapid response and mitigation efforts to minimize risk exposure.
Centralized Management
Access centralized management and reporting functionalities through the myorbik.com portal, providing a unified view of your organization’s security posture and vulnerability landscape. This centralized approach streamlines oversight and facilitates efficient decision-making processes regarding cybersecurity measures.
Alerts and Reporting
Receive instant notifications of new vulnerabilities affecting your products, ensuring timely awareness and enabling prompt remediation actions to address emerging security risks. Stay informed about the evolving threat landscape and take proactive steps to safeguard your systems and data.
Software Supply Chain Risk Management
Automate vulnerability scanning processes to continuously monitor your environment for security weaknesses. Leverage automated tools to conduct comprehensive scans and identify potential vulnerabilities, allowing for proactive risk mitigation and strengthening of your organization’s security posture.
Support and Deployment
Access technical support for installation, setup, configuration, and general usage of the myorbik.com platform. Benefit from expert assistance to ensure smooth deployment and effective utilization of the vulnerability management tool, maximizing its value in enhancing your organization’s cybersecurity defenses.
Customization
Customize settings and reports according to your organization’s specific requirements and preferences. Tailor the myorbik.com platform to align with your unique cybersecurity objectives and operational workflows, ensuring optimal functionality and relevance to your organization’s security needs.